Embedded Linux boot process
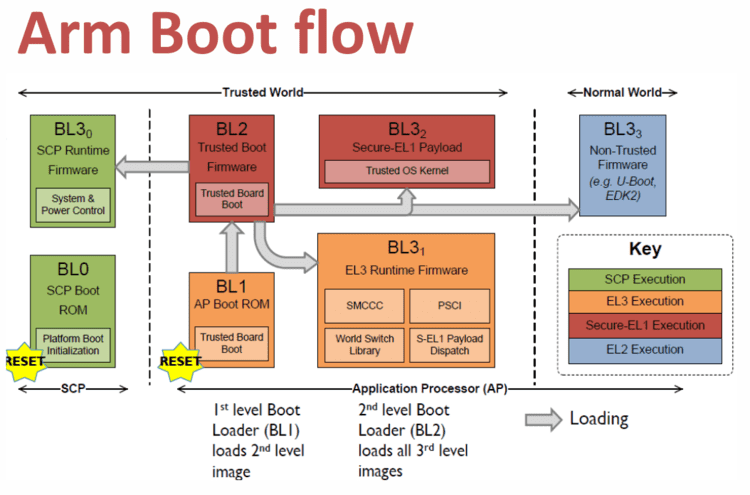
BL1
This stage begins execution from the platform's reset vector in trusted ROM at EL3. BL1 code starts at
0x00000000(trusted ROM) in the FVP memory map. The BL1 data section is placed at the start of trusted SRAM,0x04000000. The functionality implemented by this stage is as follows.
- BL1 performs minimal architectural initialization as follows.
- Exception vectors
- MMU setup
- Control register setup
- Platform initialization
- BL2 image load and execution
- BL1 loads a BL2 raw binary image from platform storage, at a platform-specific base address
- BL1 passes control to the BL2 image at Secure EL1, starting from its load address
- BL1 also passes information about the amount of trusted SRAM used and available for use. This information is populated at a platform-specific memory address
BL2
BL1 loads and passes control to BL2 at Secure-EL1. BL2 is linked against and loaded at a platform-specific base address (more information can be found later in this document). The functionality implemented by BL2 is as follows.
- Architectural initialization
- Platform initialization
- BL3-0 (System Control Processor Firmware) image load
- BL2 loads the optional BL3-0 image from platform storage into a platform-specific region of secure memory
- BL3-1 (EL3 Runtime Firmware) image load
- BL3-2 (Secure-EL1 Payload) image load
- BL2 loads the optional BL3-2 image from platform storage into a platform- specific region of secure memory
- BL3-3 (Non-trusted Firmware) image load
- BL2 loads the BL3-3 image (e.g., UEFI or other test or boot software) from platform storage into non-secure memory as defined by the platform (0x88000000 for FVPs)
- BL3-1 (EL3 Runtime Firmware) execution
- BL1 passes control to BL3-1 at the specified entrypoint at EL3
- BL2 relies on BL3-1 to pass control to BL3-3 once secure state initialization is complete
BL3-1
The image for this stage is loaded by BL2 and BL1 passes control to BL3-1 at EL3. BL3-1 executes solely in trusted SRAM. BL3-1 is linked against and loaded at a platform-specific base address (more information can be found later in this document). The functionality implemented by BL3-1 is as follows.
- Architectural initialization
- Platform initialization
- GICv2 initialization
- GICv3 initialization
- Power management initialization
- Runtime services initialization
- BL3-2 (Secure-EL1 Payload) image initialization
- BL3-3 (Non-trusted Firmware) execution
Trusted SRAM
+----------+ 0x04040000
| |
|----------|
| BL2 |
|----------|
| |
|----------|
| BL31 |
|----------|
| |
|----------|
| BL1 (rw) |
+----------+ 0x04000000
Trusted ROM
+----------+ 0x04000000
| BL1 (ro) |
+----------+ 0x00000000
BL3-2
Optional BL for Security.
BL3-3
Boot software like u-boot.